Proxy
Whoer IP & Whoer Net: Secure Your Digital Identity with Nstbrowser
Master your online identity with Whoer IP and Whoer Net. Learn how to fix DNS leaks and defeat digital fingerprinting by integrating the advanced anti-detect power of Nstbrowser.
Nov 11, 2025Robin Brown
Take a Quick Look
Stop just diagnosing your privacy leaks with IP checkers and start fixing them. Try Nstbrowser today to gain full control over your digital identity and defeat advanced fingerprinting.
Key Takeaways:
- Your online identity is a complex profile composed of your IP address, network route, and a unique digital fingerprint.
- IP checkers like Whoer IP and Whoer Net are essential diagnostic tools that reveal inconsistencies in your connection, such as DNS or WebRTC leaks, which compromise your privacy.
- Digital fingerprinting (Canvas, WebGL, AudioContext) is the primary method websites use to track you, even when your IP is masked.
- To achieve true anonymity and security, you must pair the diagnostic power of IP checkers with the protective isolation of an advanced anti-detect browser like Nstbrowser.
- This guide provides a comprehensive analysis of IP checker metrics and a step-by-step guide to securing your digital identity against the most sophisticated tracking methods.
Introduction
You cannot secure what you cannot see. In the digital world, your online identity is under constant scrutiny, revealing far more than just your location. It is a complex profile composed of your IP address, network path, and a unique digital fingerprint. Tools like Whoer IP and Whoer Net act as a mirror, showing you exactly how your connection appears to the websites you visit.
This guide will move beyond a simple review to provide a deep, technical understanding of the metrics these tools test, why they matter, and, most importantly, how to use an advanced solution like Nstbrowser to fix the leaks and inconsistencies they expose. Mastering your digital identity is the first step toward achieving true online security and operational efficiency.
The Anatomy of Your Digital Identity: What IP Checkers Test
An IP checker is a diagnostic tool that analyzes your connection and system settings against known databases and tracking vectors. It provides an "anonymity score" based on the consistency of your digital signals. The most advanced checkers, like Whoer IP and Whoer Net, test far more than just your public IP address. They perform a comprehensive audit of your connection health.
1. IP and Network Metrics (Whoer IP Focus)
| Metric | Technical Mechanism | Why It Matters for Security |
|---|---|---|
| Public IP Address | Captured from the HTTP request header. | Reveals your approximate geographic location and ISP. Essential for geo-blocking and basic tracking. |
| DNS Leak Test | Loads hidden elements that trigger DNS requests. | If your DNS resolver is different from your IP location, it indicates a leak, revealing your true ISP and location despite using a proxy or VPN. |
| WebRTC Leak Test | Uses the WebRTC API to discover local and public IP addresses. | A critical leak vector in many browsers that can expose your real IP, bypassing even the most secure VPNs. |
| Time Zone & Language | Reads system settings via JavaScript. | Inconsistencies (e.g., a US IP with a Chinese time zone) are a major red flag for anti-bot systems. |
2. Advanced Fingerprinting Metrics (Whoer Net Focus)
Digital fingerprinting is the most persistent tracking method used today. It does not rely on cookies or IP addresses; instead, it uses the unique characteristics of your device's hardware and software rendering capabilities.
- Canvas Fingerprinting: Your browser is instructed to draw a hidden graphic. The way your GPU and drivers render this image creates a unique, tiny variation that acts as a persistent identifier [1].
- WebGL Fingerprinting: Similar to Canvas, this uses the WebGL API to render complex 3D graphics. The unique combination of your graphics card, operating system, and driver version results in a highly distinct signature.
- AudioContext Fingerprinting: This technique uses the Web Audio API to generate a unique noise signal. The way your audio stack processes this signal creates a unique, measurable hash, adding another layer to your digital profile.
Conclusion: If any of these metrics are inconsistent or exposed, your anonymity score drops, and you are flagged as a high-risk user or bot.
Whoer IP and Whoer Net: The Diagnostic Difference
While both tools are excellent IP checkers, they serve distinct diagnostic purposes. Using them together provides a complete picture of your online exposure.
Whoer IP: The Visible Identity Checker
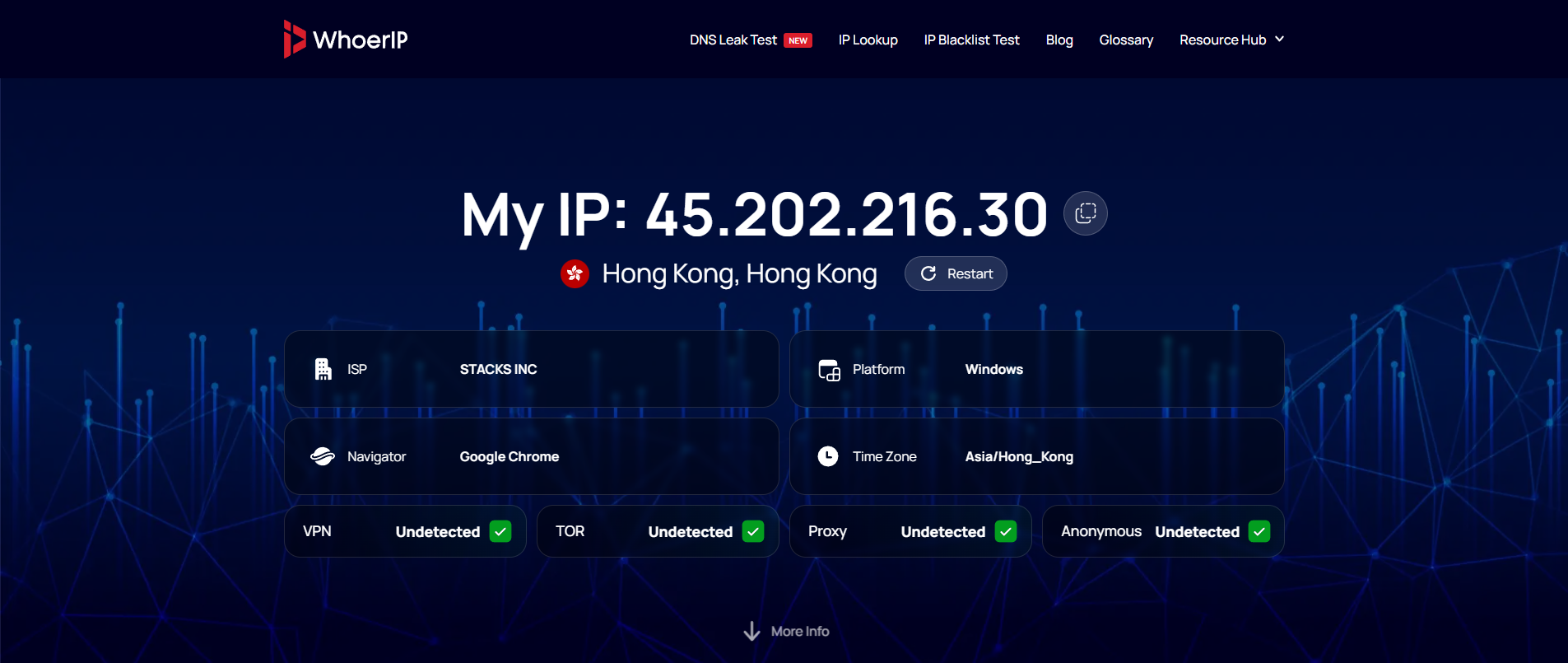
Whoer IP focuses on your visible identity—what the world sees. It answers the question: "How do I appear to websites right now?" It is the primary tool for checking for common leaks and inconsistencies.
- Primary Function: Measures the consistency between your IP, DNS, time zone, and browser language.
- Key Insight: Provides a quick, actionable anonymity score. A low score means your proxy or VPN is leaking basic information.
Whoer Net: The Network Path Analyst
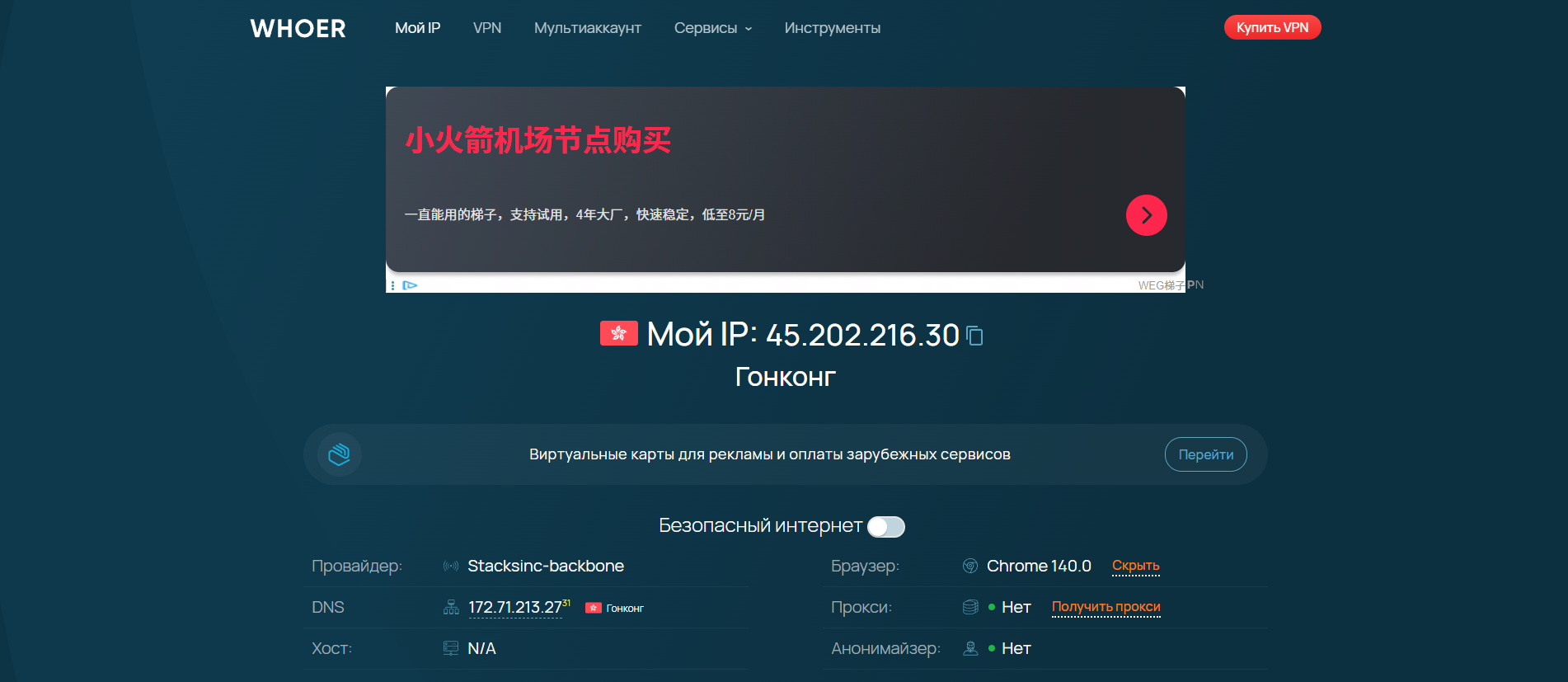
Whoer Net goes deeper, analyzing the route and quality of your connection. It answers the question: "How does my traffic travel, and does it look natural?"
- Primary Function: Analyzes the network route, latency, and, critically, the type of exit node (residential vs. data-center).
- Key Insight: Reveals hidden red flags, such as a connection that claims to be residential but is routed through a known data-center IP block. This is a crucial distinction for anti-bot systems.
Case Study 1: The DNS Leak Exposure
A remote worker uses a VPN to access a corporate network. Whoer IP shows the worker's IP address is in New York, but the DNS leak test reveals the DNS resolver is still located in their home city of London. This inconsistency immediately flags the connection as suspicious, potentially leading to a security alert or access denial. The IP checker provided the necessary diagnostic information to fix the VPN configuration.
Case Study 2: The E-commerce Analyst
An e-commerce analyst needs to check product listings from 10 different countries. They use Nstbrowser to create 10 isolated profiles, each assigned a proxy from a different country. Nstbrowser ensures that each profile has a unique digital fingerprint and that the system time zone and language are automatically set to match the proxy's location. When the analyst runs Whoer IP inside each profile, the anonymity score is 100%, allowing them to browse without being flagged as a suspicious, multi-identity user.
Go Beyond IP Testing — Strengthen Your Privacy with Nstbrowser
After using Whoer IP and Whoer Net to check how your online identity appears, the next step is to control your browsing profile.
That’s where the Nstbrowser comes in — a privacy-focused tool designed for users who need stronger isolation and precise connection management.
Nstbrowser Antidetect Browser offers two powerful features that work perfectly with IP detection tools like Whoer IP and Whoer Net:
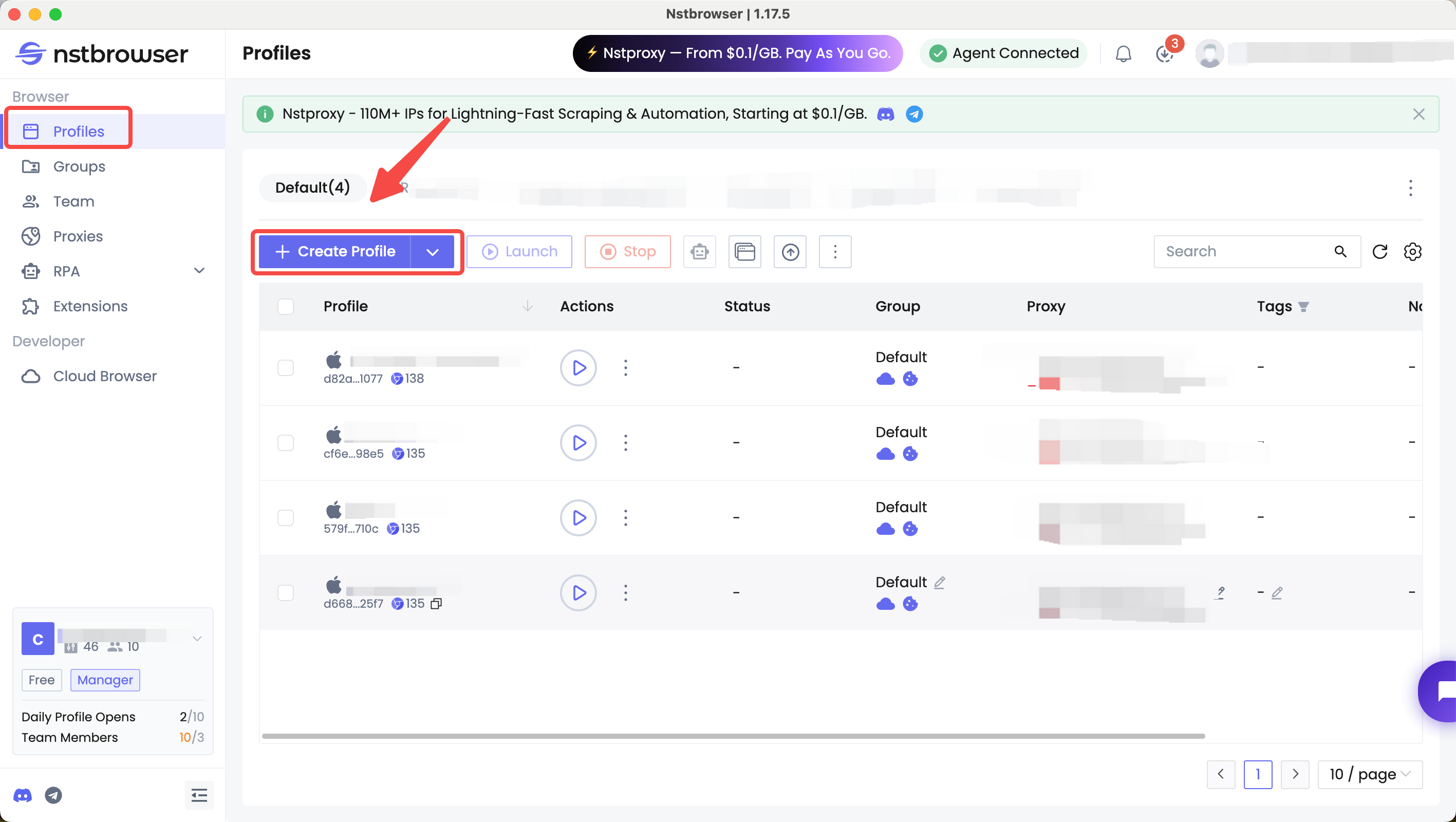
🧩 Profile Isolation
Nstbrowser allows you to create and manage multiple isolated profiles. This means cookies, fingerprints, cache, and local data do not mix between profiles.
For digital marketers, testers, or researchers who manage multiple online accounts, this isolation keeps every identity independent — avoiding cross-tracking or data leaks that can expose your true IP or system details.
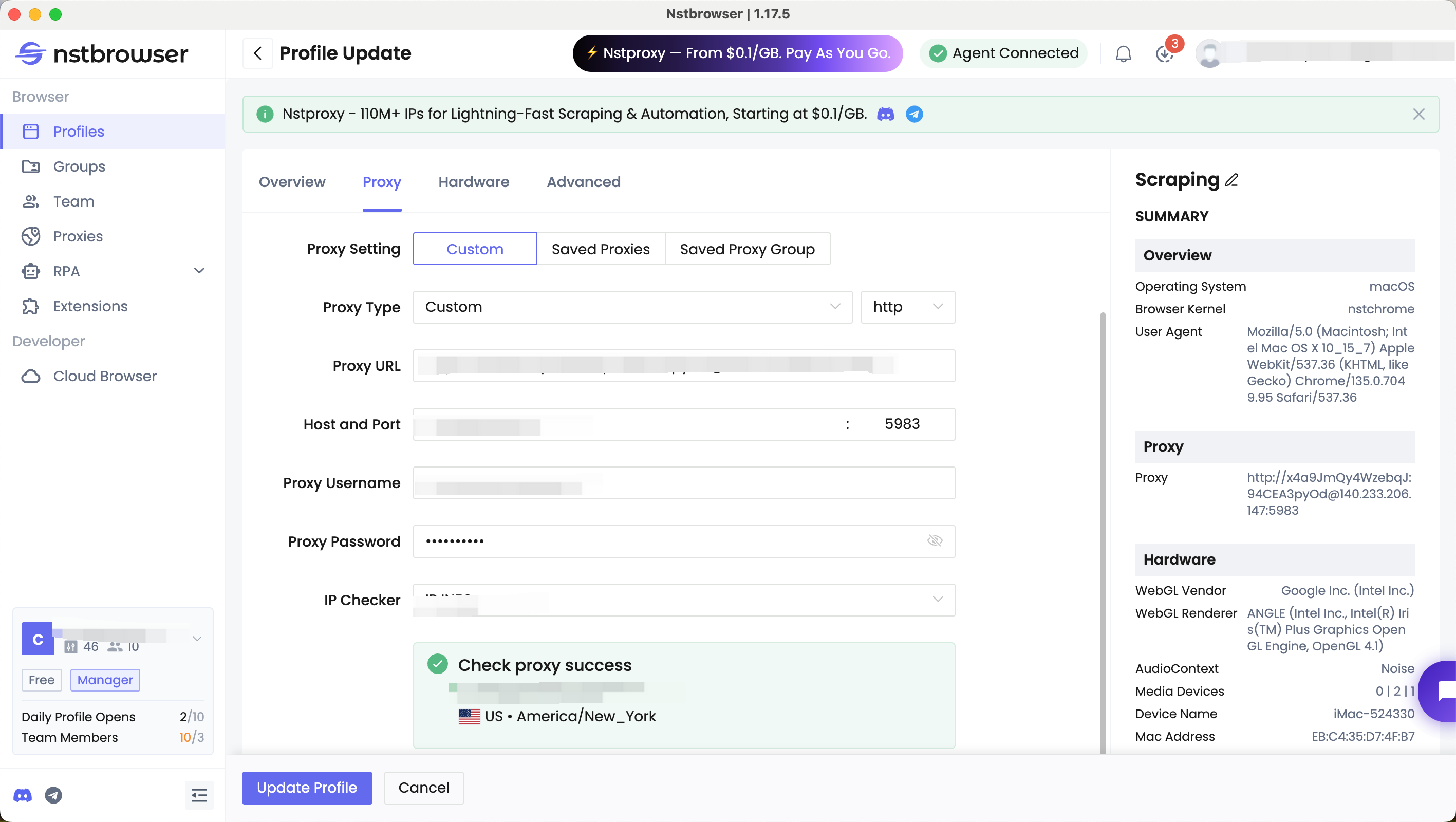
🌐 Proxy Configuration
Nstbrowser makes proxy settings simple and flexible. You can assign a unique proxy to each profile and click Checking Proxy to verify that your connection is stable and active.
This combination helps ensure that your traffic routes match your chosen region, and your browser signals align with your visible IP — boosting both credibility and security.
Why Nstbrowser is the Essential Tool for Digital Identity Control
While IP checkers are excellent for diagnosis, they offer no protection. Nstbrowser provides the necessary control to implement the fixes.
| Feature | IP Checker (Diagnostic) | Nstbrowser (Protective/Control) |
|---|---|---|
| Primary Role | Detects leaks and inconsistencies. | Prevents leaks and creates consistent identities. |
| Fingerprint | Reports the exposed fingerprint. | Spoofs and isolates the fingerprint (Canvas, WebGL, etc.). |
| Session Management | None. | Creates completely isolated, non-contaminating profiles [3]. |
| Goal | Audit and inform. | Secure and scale online operations. |
For professionals managing multiple accounts, conducting market research, or engaging in secure data extraction, Nstbrowser is not an alternative; it is the necessary next step after using diagnostic tools. It turns the red flags raised by Whoer IP and Whoer Net into green lights.
Frequently Asked Questions (FAQ)
1. Can a VPN fix all the issues raised by Whoer IP and Whoer Net?
No. A VPN primarily masks your IP address and encrypts your traffic. While it can fix IP and DNS leaks, it cannot fix the digital fingerprinting issues (Canvas, WebGL, AudioContext) or prevent time zone/language inconsistencies, which are the primary red flags for modern anti-bot systems.
2. What is the most critical metric to check on Whoer IP?
The most critical metric is the DNS Leak Test. If your DNS is leaking, your true location is exposed, regardless of your proxy or VPN. The second most critical is the consistency between your IP location and your system's time zone/language settings.
3. How often should I check my identity with an IP checker?
You should check your identity every time you set up a new proxy, change your network, or before logging into a high-value account. Once you are using Nstbrowser, you only need to verify the profile once upon creation.
4. What is the difference between Whoer IP and Nstbrowser?
Whoer IP is a diagnostic tool that tells you what is wrong with your connection. Nstbrowser is a protective tool that allows you to fix those issues by creating a unique, isolated, and consistent digital identity.
5. Is Nstbrowser only for multi-account management?
No. While excellent for multi-account management, Nstbrowser is also essential for single-account security, market research, ad verification, and any task where maintaining a consistent, high-anonymity digital identity is required.
Conclusion and Call to Action
Your digital identity is your most valuable asset online. Diagnostic tools like Whoer IP and Whoer Net are indispensable for revealing the vulnerabilities in your connection, from simple DNS leaks to complex digital fingerprint exposure. However, diagnosis without a solution is insufficient.
To truly secure your operations and ensure a consistently high anonymity score, you must move beyond simple IP masking. You need a tool that gives you granular control over your entire digital profile.
Ready to stop reacting to red flags and start proactively controlling your online identity?
Try Nstbrowser today and turn the vulnerabilities exposed by IP checkers into an ironclad defense.
References
- Canvas, Audio and WebGL: an in-depth analysis of fingerprinting technologies. Octo Browser Blog. Octo Browser Blog
- Nstbrowser Anti Detect Browser: Advanced Multi-Account. Nstbrowser Wiki. Nstbrowser Wiki
- Anti-detect browser - Nstbrowser. Nstbrowser Product Page. Nstbrowser Fingerprint Browser
- Advanced tracking and fingerprinting protection guide 2025. Pixelscan. Pixelscan
- Digital Fingerprinting in Cybersecurity: OS, Nmap, & More. Bitsight. Bitsight
- Nstbrowser Anti-Detect Bot Solution. Nstbrowser. Nstbrowser Anti-Detect
More






